The choice of the best in the business



















































































































































Power Up Your Cyber Stack
Tjakrabirawa brings together three powerhouse services trusted by banks, telcos, tech giants, and the public sector across Indonesia.
Cyber Security Insurance
Because some risks can't be patched. Our insurance service helps you shift liability, reduce financial exposure, and bounce back stronger.
Cybersecurity Scorecard
Quantify your security like a pro. Our scorecard lets you measure, benchmark, and communicate security posture across the boardroom and the SOC.
Rapid Security Assessment
Pinpoint your biggest digital risks in days, not months. Our rapid audit gives you instant clarity on your security posture before attackers get curious.
Power Up Your Cyber Stack
Tjakrabirawa brings together three powerhouse services trusted by banks, telcos, tech giants, and the public sector across Indonesia.
Cyber Security Insurance
Because some risks can't be patched. Our insurance service helps you shift liability, reduce financial exposure, and bounce back stronger.
Cybersecurity Scorecard
Quantify your security like a pro. Our scorecard lets you measure, benchmark, and communicate security posture across the boardroom and the SOC.
Rapid Security Assessment
Pinpoint your biggest digital risks in days, not months. Our rapid audit gives you instant clarity on your security posture before attackers get curious.
Cyber Attack Over The Year
$ 20,000,000
1.5 Tb BSI personal and financial information loss due to the ransomware attack.
Source: Bank Info Security
$ 14,400,000
Indodax cyber attack potential loss of unauthorized access and security lapses by North Korea Hacker.
Source: Bank Info Security
1,300,000,000
Ministry of Home Affairs, Kominfo personal data was scattered online.
Source: Restofworld
26,000,000,000
POLRI user data spread out: names, employee numbers, phone numbers.
Source: Restofworld
26,000,000
Indihome user data spread out: browsing history, locations, and others.
Source: Restofworld
17,000,000
PLN user personal data spread out: customer IDs, full names, addresses.
Source: Restofworld
The Security Trifecta That Actually Moves the Needle
It's not just about tools—it's about timing, context, and risk control. Tjakrabirawa's combined offering gives you deep visibility, strategic clarity, and financial fallback in one integrated flow.
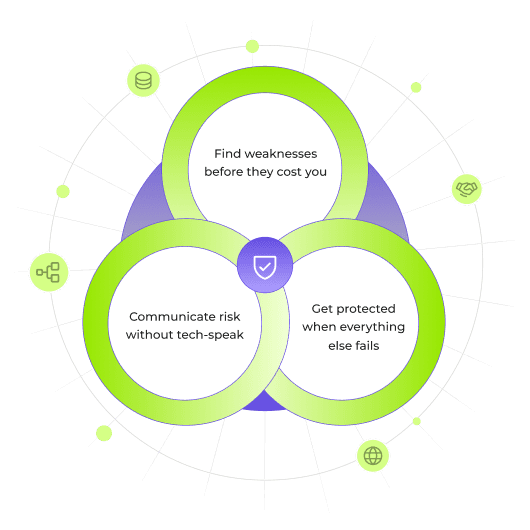
Built for Leaders
Who Want the Full Picture
Key Benefits You Can Count On
Get the tools to level up your security
What's your plan?
Security
Made
Simple—for
Empowering Businesses with Next-Gen Cybersecurity Solutions.
Cybersecurity Latest News
UU PDP Sudah Berlaku Tapi... Benarkah Data Kita Masih Jadi Incaran Empuk?
Pernah ngerasa gak kalau baru aja ngomongin suatu barang, tiba-tiba iklannya langsung muncul di media sosial kamu? Bayangin kamu lagi asik scrolling, tapi di balik layar ada ribuan data pribadi kamu yang mungkin sedang berpindah tangan tanpa kamu sadari sedikit pun. Kebanyakan orang salah kaprah dan merasa aman karena Indonesia sudah punya aturan hukum, padahal kenyataannya regulasi tanpa eksekusi itu cuma macan kertas. Di artikel ini, kamu bakal nemuin fakta pahit kenapa UU Perlindungan Data Pribadi (UU PDP) kita masih jauh dari kata efektif untuk melindungi jempol kamu.
See more
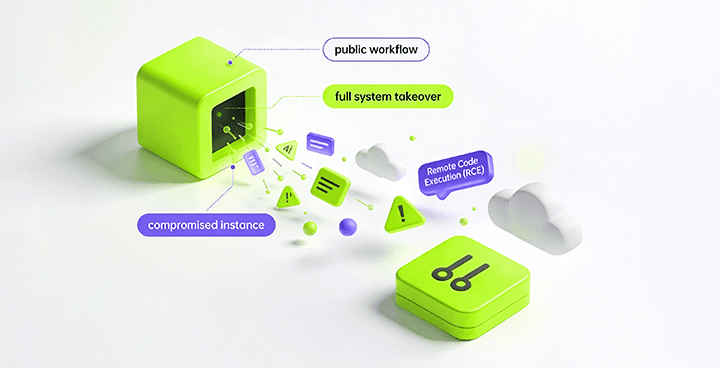
n8n Hacked From Zero Login: Satu Bug, Semua Secrets & Workflow Bocor
Pernah ngerasa gak kalau sistem otomasi yang kamu andalkan buat bikin kerjaan jadi simpel justru bisa jadi pintu masuk paling lebar buat peretas? Bayangin kamu sudah capek-capek nyusun alur kerja yang rumit, menyimpan semua kunci akses API perusahaan, hingga data pelanggan, tapi semuanya bisa dicuri cuma lewat satu celah kecil tanpa peretas perlu login sama sekali. Kebanyakan orang salah kaprah dan merasa aman selama mereka sudah pasang password yang kuat, padahal kenyataannya ada bug fatal yang bisa bikin pertahanan itu gak berguna sama sekali. Di artikel ini, kamu bakal nemuin fakta mengerikan di balik kerentanan kritis bernama Ni8mare yang baru saja mengguncang platform n8n.
See more
Kesepakatan Rp944 Miliar! Kemhan Gandeng ITSEC Asia Perkuat Pertahanan Siber AI
Pernah ngerasa gak kalau ancaman perang zaman sekarang bukan lagi soal adu fisik, tapi soal adu kecanggihan algoritma di ruang siber? Bayangin sebuah negara bisa lumpuh total hanya karena serangan digital yang tidak terlihat mata, namun dampaknya bisa merusak seluruh infrastruktur vital. Kebanyakan orang salah kaprah dan menganggap pertahanan negara cuma soal alutsista fisik, padahal kenyataannya ancaman berbasis kecerdasan buatan atau AI sudah ada di depan mata. Di artikel ini, kamu bakal nemuin fakta di balik kerja sama raksasa senilai Rp944 miliar antara Kementerian Pertahanan (Kemhan) dan ITSEC Asia untuk membentengi kedaulatan digital Indonesia.
See more
© 2025 Tjakrabirawa Teknologi Indonesia. All Rights Reserved.